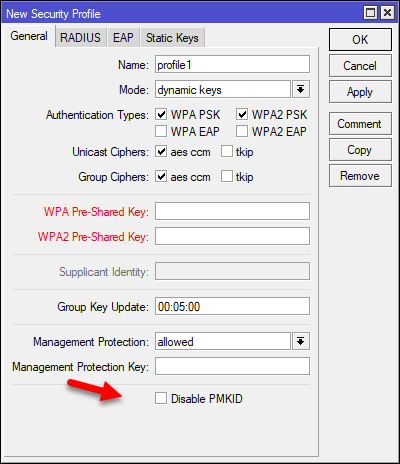
طبق اطلاعیه بلاگ سایت میکروتیک در مورد حملات Brute Force برروی WPA2 امکان جدیدی بر روی ورژن های ۶.۴۰.۹ و ۶.۴۲.۷ قراد داده شده تا از این آسیب پذیری در امان باشید.
با فعال کردن (در واقع غیر فعال کردن PMKID ) قسمتی که در تصویر زیر مشخص شده میتوانید جلوی نفوذ به اکسس پوینت خود را بگیرید.
It has come to our attention that a new way of brute force attack based on WPA2 standard using PMKID has come to light.
This attack actually is a brute force attack on WPA2 preshared key. The reason this attack is considered effective is because it can be performed offline, without actually attempting to connect to AP, based on a single sniffed packet from a valid key exchange.
This problem is not a vulnerability, but a way how wireless AP password can be guessed in an easier way.
In order to mitigate this type of attack you should use strong password that is hard to brute force. Using access-list also helps to protect your network, because the attacker needs to be authenticated first.
To eliminate possibility of this attack entirely you can use WPA-PSK (do not forget to use aes-ccm encryption!). WPA-PSK does not include the field that is used to verify the password in this attack.
We have also added the option to disable sending PMKID in handshake message 1 in WPA2-PSK. Disabling it will also protect your network against this attack. This option is available in RouterOS versions 6.40.9, 6.42.7 and 6.43 (from rc56).